OAUTH2 Tokens
Wink Login SDK provides app developer with standard OAUTH tokens ( Access Token, ID Token and Refresh Token ), this generated with a special provider from our WinkSeed and WinkToken. These tokens have to be decrypted by the app developer to receive the needed information from the included claims and scopes.
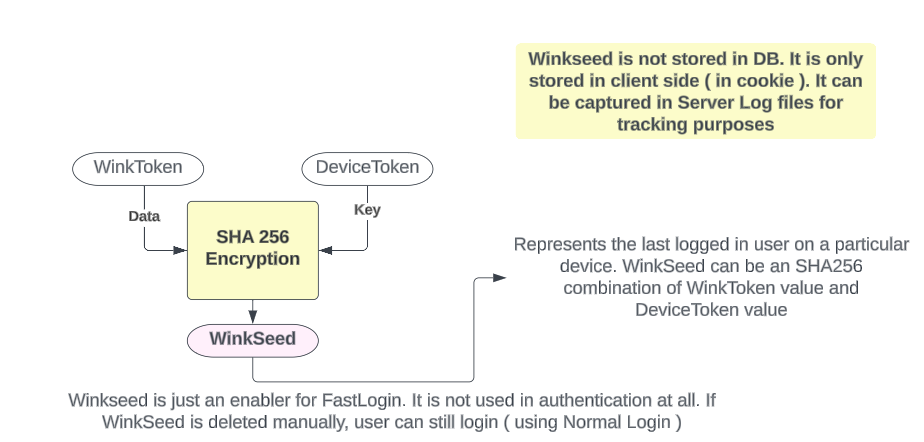
Wink Login using the WinkId (User) and Clientid (client) can generate a WinkToken. Also, for every new device, a DeviceToken is created by Wink Server. Finally we generate a WinkSeed (JWE) with a special algorithm using the DeviceToken to encript or unencript the info there
The provided tokens are:
ID Token / Access Token
These tokens contains a tokenized version of the user profile. An example of the decrypted version of these tokens is shown in the box here.
Some of the useful claims in the token are:
- Exp: expiry date and time
- azp: ClientID of the host app
- Sub: WinkToken for the Recognized user ( should be mapped to UUID of the user in the app developer system)
- User Profile:
- given_name = FirstName
- family_name = LastName
- phone_number = MobileNumber
- email = email
- preferred_username = WinkTag ( unique username of this user across the entire Wink ecosystem )
In order to use the Access Token and detokenize the user profile to clear values, see the API section titled Validating the Tokens
Access Token Example
{
"exp": 1724059661,
"iat": 1724059361,
"jti": "23ad82d3-a920-4987-9bb4-4bdd750e7f6e",
"iss": "https://stageauth.winkapis.com/realms/wink",
"aud": "account",
"sub": "883a9556-534a-4e4a-a871-480c91b8e6e2",
"typ": "Bearer",
"azp": "winkwallet",
"nonce": "a7e524d7-e851-4b0e-97e0-01c8a6d797a2",
"session_state": "3c2816d2-5650-4a9d-aae6-5c593ee3eef4",
"acr": "0",
"allowed-origins": [
"*"
],
"realm_access": {
"roles": [
"offline_access",
"default-roles-wink",
"uma_authorization"
]
},
"resource_access": {
"account": {
"roles": [
"manage-account"
]
}
},
"scope": "openid profile email",
"sid": "3c2816d2-5650-4a9d-aae6-5c593ee3eef4",
"email_verified": true,
"phone_number": "tok_sandbox_uS3QqU33evypwDfJRpdkq2",
"oid": "320922b8-6688-4bc1-86d3-e6952dcd004c",
"preferred_username": ";stage-vjhk+sf9-v",
"given_name": "tok_sandbox_uS3QqU33evypwDfJRpdkq2",
"family_name": "tok_sandbox_uS3QqU33evypwDfJRpdkq2",
"email": "tok_sandbox_uS3QqU33evypwDfJRpdkq2"
}
Refresh Token
This token can be used to extend the expiry date of all 3 tokens by 5 min. This token (when decryoted) looks like the box here.
This token has an expiry period of 30 min and can be used to extend the expiry period of all tokens ( including the refresh token itself ) by 5 min but must be called while all the tokens are still valid.
Refresh Token Example
{
"exp": 1724060229,
"iat": 1724058429,
"jti": "f1466082-70d5-4c87-89cd-062533c7c11d",
"iss": "https://stageauth.winkapis.com/realms/wink",
"aud": "https://stageauth.winkapis.com/realms/wink",
"sub": "883a9556-534a-4e4a-a871-480c91b8e6e2",
"typ": "Refresh",
"azp": "winkwallet",
"nonce": "3c38c039-6ab0-4e75-888e-6cb58492d078",
"session_state": "ffa978ad-1636-45af-8e7b-c87e509e7a61",
"scope": "openid profile email",
"sid": "ffa978ad-1636-45af-8e7b-c87e509e7a61"
}
Updated about 1 year ago
Now that you have understood how Wink Login SDK works, lets explore how easy it is to integrate Wink Login into your application Front End and Back End flows
